Worst Apps for Privacy are mobile applications that extensively collect, share, and monetize user data through aggressive harvesting techniques, often gathering twenty or more data categories while maintaining partnerships with multiple advertising networks and third - party data brokers. Many of these apps collect user data primarily to serve ads and generate revenue through targeted ads, which is a major privacy concern.
The specific applications with the most invasive data collection practices, the types of personal information being harvested, how this data is shared with advertising networks and third - party companies, the systematic exploitation patterns that exceed functional requirements, and the hidden costs of free digital services is explored in this post, below.
Key Takeaways
- Meta’s Messenger ranks as the most invasive app with a 100/100 privacy score, collecting over 20 different data types.
- Pinterest, Lyft, Amazon Shopping, and DoorDash also rank among the worst privacy offenders with scores above 66/100.
- Weather apps pose greater privacy risks than social media, with persistent location tracking even after user opt - out.
- Popular mobile game titles, such as Candy Crush and Roblox, are among the top downloads and pose significant privacy risks due to their data collection practices, averaging 6.1 trackers per installation.
- Meta’s tracking pixel operates on 30% of popular websites, enabling comprehensive cross - platform user profiling and data harvesting.
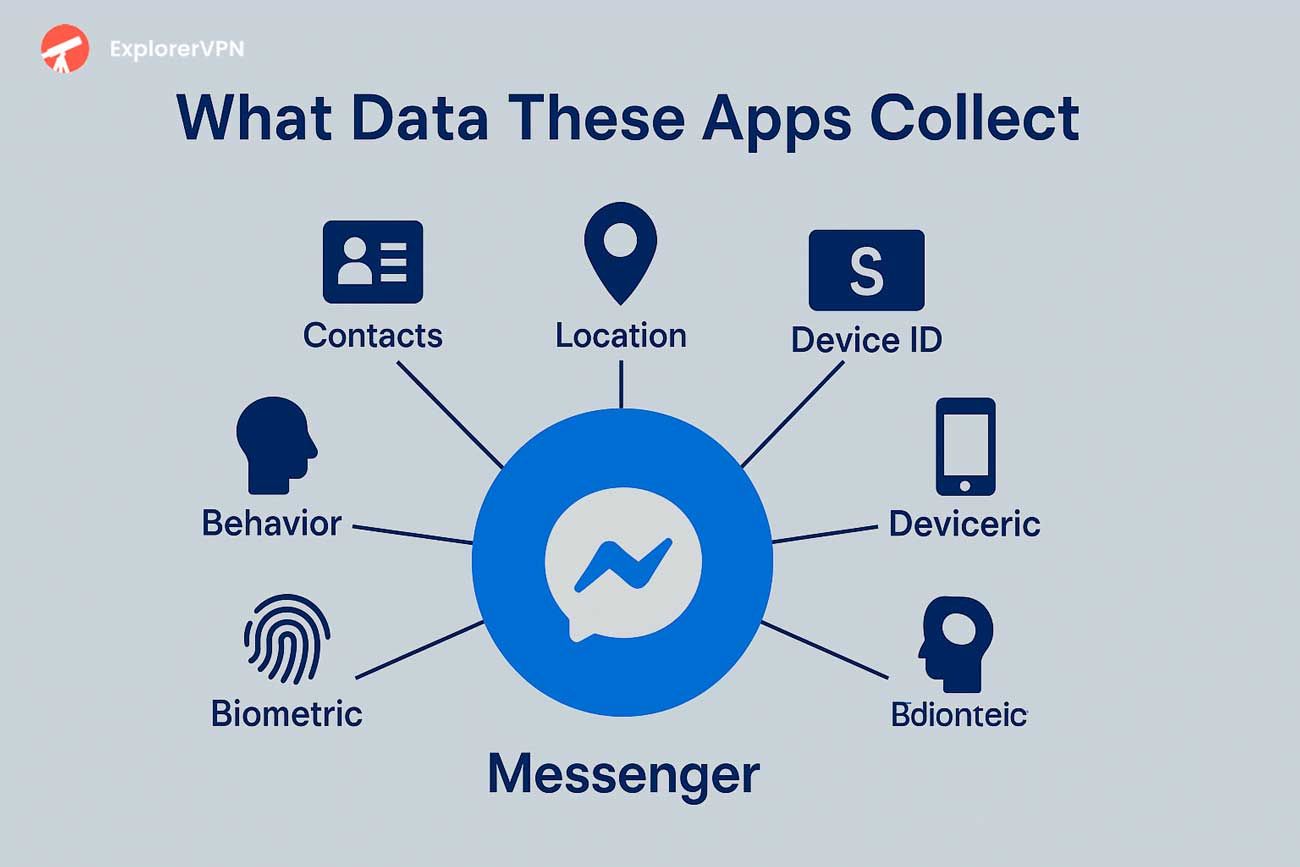
Example of data collection, Messenger app.
Why Some Apps Are So Invasive?
Apps collect invasive data primarily for advertising revenue, data monetization, and AI training purposes.
- 90% of free mobile applications rely on advertising as their primary income source, driving extensive data harvesting practices.
- Social media platforms share 79% of user data for promoted content delivery.
- Facebook collects 57% exclusively for targeted advertising campaigns.
In many apps, this extensive data collection and privacy invasion serve the interests of tech companies and advertisers - not the benefit of the user.
Data monetization represents a growing threat beyond traditional advertising models. Applications increasingly exploit collected information to train large language models, requiring massive datasets comprising personal information. Many apps, especially business - oriented services, are involved in selling approximately 50% of collected user data to third - party advertisers, creating additional revenue streams from user privacy violations.
User consent remains systematically undermined through deliberately complex privacy policies. 24 out of 27 privacy policies require college - level education to comprehend, creating intentional obfuscation that enables continued data exploitation while appearing to provide user choice.
The convergence of these factors - advertising revenue dependence, AI development data needs, and deliberately obscured consent processes - creates a technology ecosystem where invasive data collection becomes financially incentivized and legally protected through complexity.
How Apps Collect and Use Your Personal Data?
Collecting data is a core function of many apps, involving the gathering of not just basic details but also other information such as device identifiers and behavioral patterns. Apps collect personal data through:
- Unencrypted transmission pathways
- Third - party SDK integration
- Contact information sharing
- Cross - platform tracking mechanisms
Enencrypted transmission pathways represent a significant vulnerability, with 20% of mobile applications exposing sensitive user content - including photos, videos, and audio files - to external servers without proper security protocols. This lack of encryption during data transfer creates opportunities for unauthorized access to highly personal multimedia content.
Third - party SDK integration operates as a hidden data collection method where embedded tracking mechanisms harvest user information without explicit user knowledge or consent. These software development kits function within applications to gather behavioral data, location information, and usage patterns, which are then transmitted to external data brokers, advertising networks, and other third parties. In many cases, apps share the collected data with multiple entities - including advertisers and analytics providers - increasing the risk of privacy breaches.
Contact information sharing affects 14% of analyzed applications through unauthorized connections to external servers. These applications access user contact lists, phone numbers, email addresses, and associated metadata, often transmitting this information to third - party services for marketing purposes or social graph analysis.
Cross - platform tracking creates comprehensive user profiles by linking device identifiers across multiple internet - connected devices. This tracking method connects smartphones, tablets, computers, and smart home devices to build detailed behavioral profiles that follow users across their entire digital ecosystem, enabling targeted advertising and data monetization strategies.

Worst apps for privacy
The Most Privacy - Invasive Apps of 2025
Meta’s Messenger scored 100/100 as the most privacy - invasive app of 2025, collecting over 20 data types including contacts, location, and financial information. According to Tenscope’s invasiveness index, supported by findings from the pCloud study, Messenger tops the list for its extensive data collection among popular apps.
The top five rankings for most privacy invasive apps are:
- 1. Messenger - 100/100
- 2. Pinterest - 72/100
- 3. Lyft - 69/100
- 4. Amazon Shopping - 68/100
- 5. DoorDash - 66/100
Some of these platforms are owned by the same company, increasing the potential for unified data sharing across services. These scores reflect extensive data collection practices across major platforms, with Messenger achieving the maximum possible invasiveness rating.
Photo - video applications emerged as the most invasive category, averaging 61.47/100, followed by social networking platforms. This category analysis highlights systematic privacy concerns across app types, with visual content platforms demonstrating particularly aggressive data - harvesting techniques.
80% of social media companies continue using personal information for AI training purposes despite increasing privacy regulations. Only Telegram, Twitch, and Discord explicitly prohibit such AI training practices, setting them apart from industry norms. User data is often shared with brands for marketing and advertising purposes. The widespread data utilization for machine learning demonstrates insufficient data minimization techniques across major platforms, with most companies prioritizing AI development over user privacy protection.
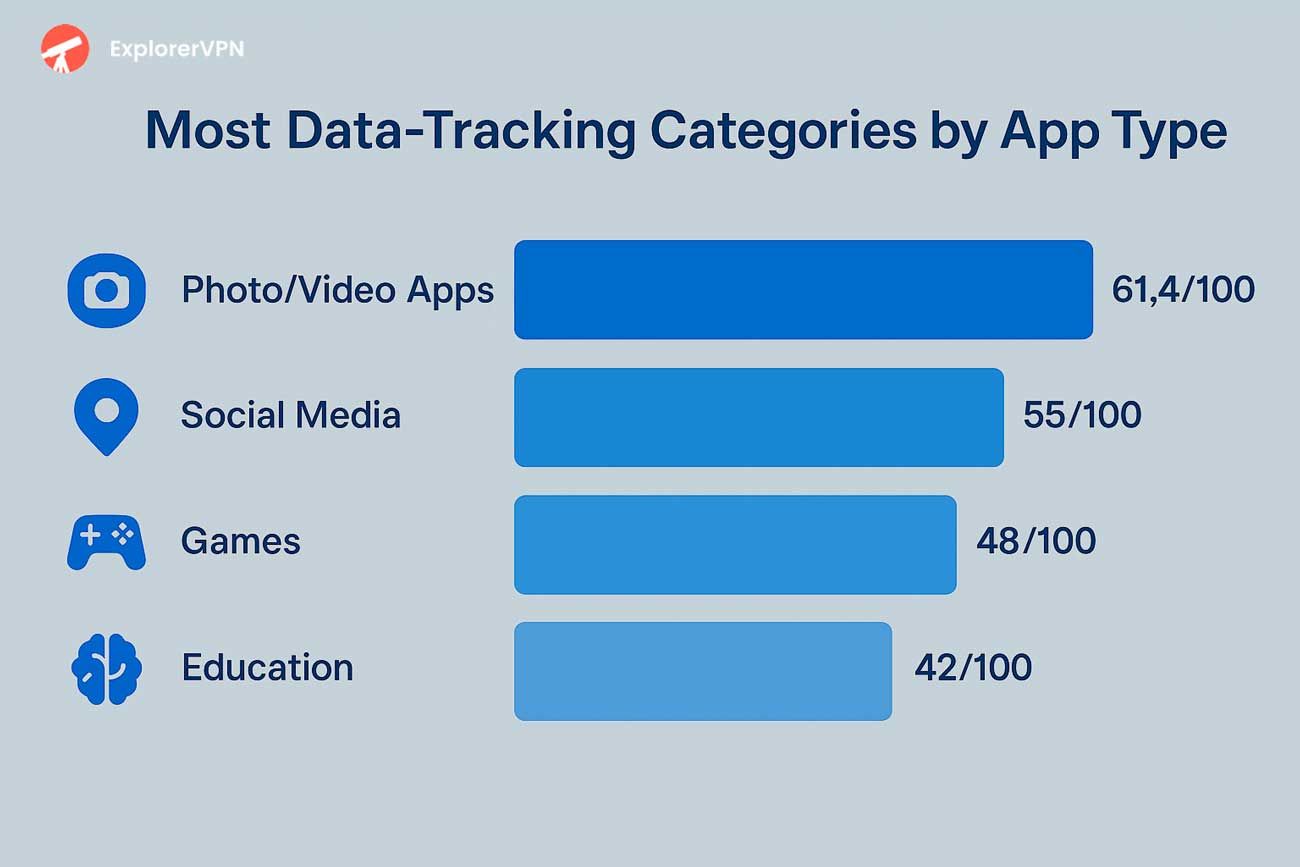
Worst app categories for your privacy
Social Media Giants and Data Harvesting (Meta, TikTok, LinkedIn, X)
Meta’s tracking pixel operates on 30% of the world’s most popular websites, enabling systematic data harvesting that extends far beyond individual applications through cross - platform tracking mechanisms. These platforms are frequent targets for cyberattacks due to the vast amount of data they collect. Meta, TikTok, LinkedIn, and X engage in extensive data collection practices that include cross - device tracking, offline purchase data harvesting, and non - user information gathering.
Meta’s data harvesting infrastructure creates comprehensive user profiles through multiple digital touchpoints, maintaining tracking capabilities even after account deletion. The company’s tracking pixel technology monitors user behavior across the internet regardless of whether individuals maintain active accounts on Meta platforms like Facebook, Instagram, or WhatsApp.
Cross - device tracking mechanisms enable these social media giants to create extensive profiles across smartphones, tablets, computers, and other connected devices. Meta and other platforms collect offline purchase data through business partnerships, encouraging enterprises to share customer interaction records and transaction histories.
Non - user information harvesting represents a significant privacy violation where platforms like Meta collect contact details and browsing history from individuals who have never created accounts. In many cases, the scale of data collection and sharing is worrying for both users and privacy advocates. Healthcare data transmission occurs through tracking pixels, with one - third of top U.S. hospitals sharing sensitive patient information with social media platforms.
TikTok’s data collection practices include location tracking, device identifiers, and behavioral analytics that create detailed user profiles. LinkedIn harvests professional data including employment history, salary information, and business connections. X (formerly Twitter) collects real - time conversation data and engagement patterns across political and social topics.
These systematic privacy violations demonstrate how Meta, TikTok, LinkedIn, and X prioritize data monetization over user privacy, creating comprehensive surveillance networks that track billions of users across digital and offline environments.
Can a VPN Protect You from Social Media Tracking?
A virtual private network (VPN) can partially mitigate social media tracking by encrypting user traffic and masking the device’s IP address, reducing the effectiveness of location - based profiling and cross - site identification. This encryption prevents internet service providers and unsecured networks from intercepting transmitted data, particularly when users access social media platforms through public Wi - Fi. Learn more about it in VPN for Facebook, Instagram or Snapchat pages.
However, VPN protection remains limited once users log into social media accounts, as most tracking occurs through cookies, browser fingerprinting, and application - level telemetry rather than network - level monitoring. Platforms like Meta and TikTok maintain persistent tracking mechanisms that operate beyond IP - based identification, linking user behavior across devices and sessions through account credentials, SDK integrations, and browser scripts.
While VPNs can obscure geographic information and block some third - party trackers, they cannot prevent direct data collection within logged - in sessions or metadata sharing between interconnected apps. Therefore, VPN usage should be viewed as a complementary privacy layer rather than a complete defense against social media data harvesting.
Messaging Apps That Aren’t as Private as You Think (Messenger, WhatsApp Business, Snapchat)
Messenger, WhatsApp Business, and Snapchat collect extensive user data including behavioral analytics, location data, interaction patterns, and biometric information despite privacy - focused marketing claims.
These messaging platforms employ sophisticated tracking mechanisms that fundamentally contradict user expectations of secure private communications. WhatsApp Business operates within Meta’s comprehensive data sharing ecosystem, allowing corporate accounts to harvest customer interaction metrics that directly feed targeted advertising infrastructure across Facebook and Instagram networks.
Snapchat’s temporary messaging format masks substantial data harvesting operations that generate $18.07 million monthly revenue through behavioral tracking - powered in - app purchases. The platform’s AR filter interactions capture biometric facial data while users believe their communications disappear permanently.
Messenger integrates with Facebook’s advertising platform, enabling cross - platform user profiling that combines messaging behavior with social media activity, search history, and website visits. These apps log user activity, such as message frequency and login events, which can be used for targeted advertising. The service tracks message frequency, contact lists, call duration, and file sharing patterns to build comprehensive user profiles.
Many messaging apps now include features that respond to user commands or voice inputs, such as digital assistants, further expanding the types of data collected and logged. These privacy vulnerabilities expose users to systematic surveillance while messaging apps monetize intimate communication patterns across global user bases. Corporate data practices transform private conversations into advertising revenue streams, with user behavioral data shared across parent company ecosystems and third - party advertising networks without explicit user awareness of the scope of data collection.
Everyday Apps That Quietly Track You (Amazon, YouTube, Google Services, PayPal)
Amazon, YouTube, Google Services, PayPal, and eBay collect biometric data through device hardware, track users through extensive app permissions including government ID verification and payment monitoring, retain personal information indefinitely, and operate under inadequate privacy regulations. eBay, as a popular online marketplace, is known for collecting and sharing substantial amounts of user data, raising privacy concerns about how personal info is tracked and accessed on the platform.
Biometric data collection by these everyday apps occurs automatically through your device’s sensors, cameras, and microphones without requiring explicit permission for each instance. Amazon’s Alexa devices continuously listen for wake words, while YouTube’s mobile app can access your camera and microphone even when not actively recording. Google Services integrate across Android devices to collect fingerprint data, facial recognition patterns, and voice prints through the operating system itself.
App permissions create extensive tracking networks where PayPal monitors transaction patterns and spending behaviors, Amazon tracks shopping habits and delivery locations, YouTube analyzes viewing patterns and search histories, and Google Services combine data across Gmail, Maps, Chrome, and other platforms. These permissions often include access to contacts, location services, storage files, and network communications that enable cross - platform user profiling. Apps may also request access to personal info, such as your date of birth, which can be used for identity verification or targeted advertising.
Data retention policies allow these companies to store user information permanently, with Amazon keeping voice recordings and purchase histories, YouTube maintaining watch history and engagement metrics, Google preserving search queries and location data across all services, and PayPal retaining financial transaction records. This indefinite storage creates comprehensive digital profiles used for targeted advertising and algorithmic recommendations.
Privacy regulations like GDPR and CCPA provide limited protection against these tracking practices, as companies continue lobbying for federal legislation that would establish uniform data transparency requirements while potentially preempting stronger state - level privacy laws.
Gaming and Kids’ Apps That Put Privacy at Risk (Candy Crush, Roblox, Reading Eggs, ABCMouse)
Casual gaming apps contain 6.1 trackers per installation on average, while educational apps have 2.12 trackers per installation, making gaming apps the highest tracker density category among mobile applications. Many of these gaming platforms are considered favorite apps by users, especially children, despite the significant privacy risks they pose.
Popular gaming platforms like Candy Crush and Roblox, along with educational apps such as Reading Eggs and ABCMouse, collect extensive user data through these tracking systems. The data collection practices remain opaque despite GDPR regulations requiring transparency, with privacy policies consistently failing to provide complete details about their data sharing ecosystems. Some of these apps are also involved in selling user data to advertisers and data brokers, often without user awareness or consent.
Educational apps targeting children show marginally better privacy practices compared to casual gaming applications, yet both categories expose kids to significant privacy risks. The sharing ecosystem details are deliberately obscured in privacy documentation, preventing parents from understanding how their children’s personal information flows between third - party advertisers, analytics companies, and data brokers integrated into these popular applications.
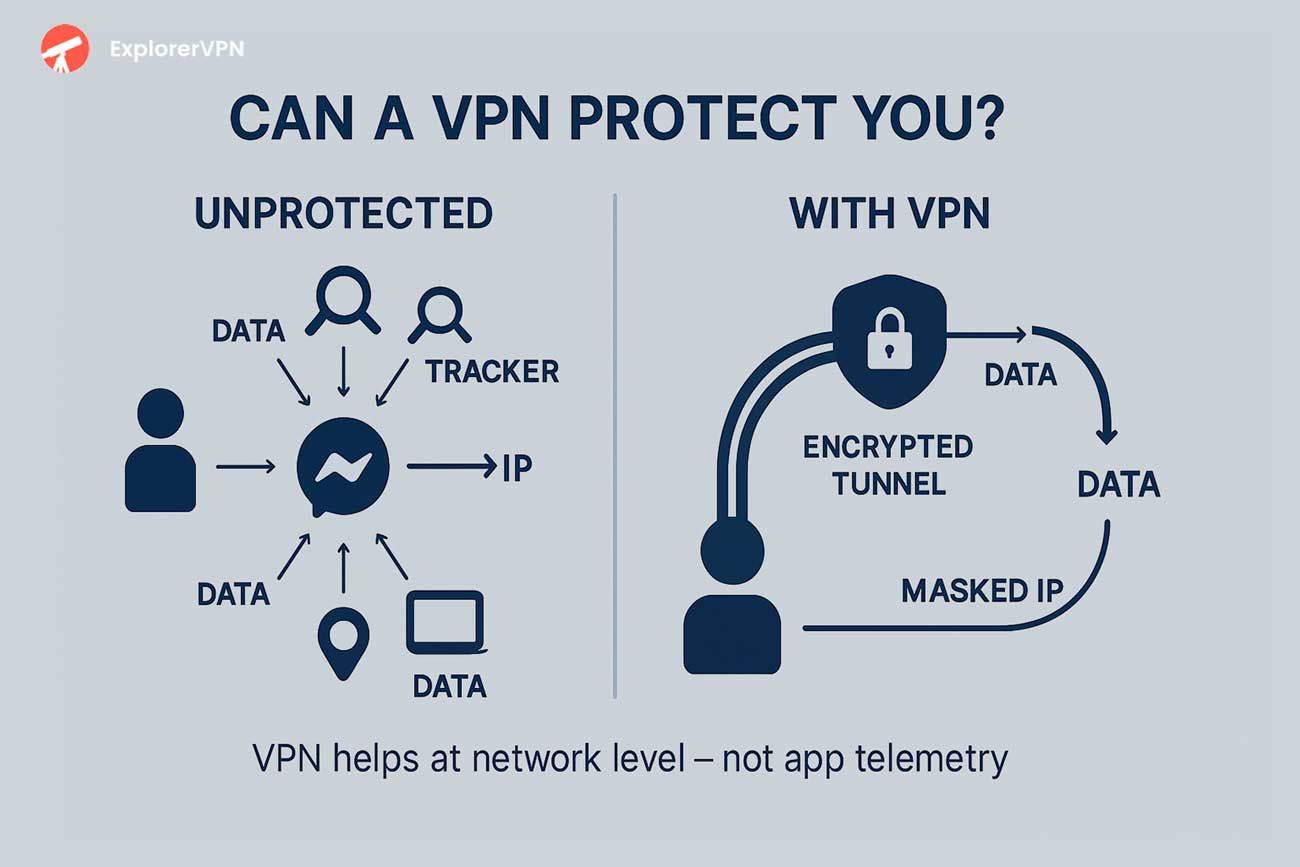
Yes, VPN can help, but at network level, not app.
Can a VPN help in the case of gaming & kids’ apps privacy risk?
A virtual private network (VPN) can offer partial protection when using gaming and educational apps by encrypting network traffic and masking the user’s IP address, thereby reducing exposure to external interception on public Wi - Fi networks. This level of protection helps prevent unauthorized third parties from monitoring transmitted data, particularly in unsecured environments frequently accessed by children. Learn more about it in Valorant, World of Tanks or Mobile Legends use cases.
However, a VPN cannot prevent in - app data collection or the transmission of personal information gathered through embedded tracking software, third - party SDKs, and analytics modules. Platforms like Candy Crush, Roblox, Reading Eggs, and ABCMouse rely heavily on internal trackers and advertising networks that operate independently of network - level encryption. These mechanisms collect behavioral data, usage patterns, and device identifiers regardless of VPN usage.
While a VPN can obscure geographic information and mitigate some risks associated with open networks, it cannot block internal app telemetry, ad network integrations, or cross - platform user profiling. As a result, VPN use should be considered a supplementary privacy measure rather than a comprehensive defense, especially for protecting children’s data within gaming and educational environments.
Weather apps are hidden privacy trackers
Seemingly Harmless Apps That Sell Your Data (Weather, Dating, Language Learning Apps)
Weather apps pose greater privacy risks than social media platforms through invasive data collection practices, with 13 of 15 weather applications automatically enabling precise geolocation tracking upon installation. Users should be aware that when they download and install these seemingly harmless apps, they may unknowingly expose their personal data to significant privacy risks.
- The Weather Channel represents the most systematic example of weather data exploitation, generating millions through third - party sales while misleading users about consent requirements.
- IBM’s Weather Channel shared user data with 42 distinct third - party recipients without explicit user consent, demonstrating how seemingly innocent weather services function as commercial data brokerages.
Five weather apps continued location monitoring even after users disabled location services, using persistent tracking mechanisms that collect:
- Comprehensive user profiles
- Sleep schedules
- Usage patterns
- Device identifiers
- Precise geolocation coordinates
Users typically believe location sharing supports legitimate weather services, unaware that their data feeds extensive monetization networks. Weather applications demonstrate more invasive collection practices than social media platforms because users grant location permissions without understanding the commercial exploitation occurring behind basic forecast functionality.
When installing these apps, users should carefully review privacy warnings and permissions requested, as these often indicate the true extent of data collection and sharing.
The deceptive privacy practices extend beyond simple location tracking, with weather apps building detailed behavioral profiles that exceed the data collection scope of many social media platforms while operating under the guise of providing essential weather information.
Free apps are hidden cost of your privacy
Why Country of Origin Matters in Data Collection?
Country of origin determines which data protection laws apply to apps and user information, creating vastly different privacy safeguards depending on where companies are based.
Data sovereignty requirements vary dramatically between regulatory models across major jurisdictions. China's "Beijing Effect" mandates domestic storage with mandatory government security reviews for all user data collected by Chinese companies. The EU's GDPR establishes strict extraterritorial privacy standards that apply globally to European companies and any organization processing EU citizen data. United States companies operate under sectoral privacy laws with fewer comprehensive protections compared to European standards.
These regulatory differences mean apps from different countries operate under fundamentally different privacy expectations and legal obligations. Data residency laws in countries like China, Russia, and India actually facilitate government access through physical server raids and direct data requests, contradicting their marketed privacy protection purposes. This creates jurisdiction - dependent vulnerability levels where users face varying degrees of government surveillance and data access depending on their chosen app's country of origin.
Cross - border data transfers become particularly complex when apps must comply with multiple conflicting regulatory frameworks, often forcing companies to adopt the most restrictive standards or implement region - specific data handling practices.
Are “Free” Apps Worth the Privacy Tradeoff?
Free apps typically extract more value through data collection than they provide in services, creating an unfavorable exchange where users surrender extensive personal information for limited functionality. These apps are often highly convenient, making it easier for users to accept privacy risks in exchange for ease of use.
The freemium business model systematically restricts essential features while maximizing data harvesting opportunities. Jotform limits free users to 100 monthly submissions while continuously collecting detailed form data throughout the restricted period. SurveyPlanet prevents data downloading in free versions, maintaining indefinite platform control over collected user information.
Security features remain locked behind paywalls - HIPAA compliance appears exclusively in paid tiers, forcing users to choose between privacy protection and cost savings. Meanwhile, Firebase and AppsFlyer expand tracking capabilities by gathering crash reports, behavioral analytics, and purchase insights without providing monetary compensation to users.
These privacy extraction methods compound as free applications prioritize data monetization over user control. The asymmetrical value exchange becomes evident when considering that behavioral data, form submissions, and usage patterns generate ongoing revenue streams for companies while users receive artificially limited functionality designed to drive premium conversions.
Practical Steps to Protect Your Privacy and Limit Data Harvesting
These digital hygiene practices establish comprehensive protection across interconnected device ecosystems, significantly reducing data exposure to commercial harvesting operations. Following these privacy practices is essential to stay safe in today’s digital environment.
How to Check App Privacy Reports Before Downloading?
Users can check app privacy reports by reviewing the App Store’s privacy labels located below app descriptions, which detail data collection practices, identity linkage, and third - party sharing before installation. These reports can also help users identify which apps share their data with third parties, highlighting potential privacy risks.
The App Store privacy nutrition labels provide standardized disclosures showing exactly what personal information apps access and how they use it. These labels cover critical data categories including location data, camera access, microphone permissions, and contact information requirements.
The privacy sections display expandable categories that reveal whether apps collect data linked to user identity or track users across other applications and websites. Data linkage indicators specifically show if collected information connects to your personal identity, while third - party sharing practices expose tracking capabilities that extend beyond the individual app. Privacy labels can indicate the extent to which apps share user data for advertising, analytics, or personalization purposes.
However, these privacy disclosures represent developer self - reported claims rather than independently verified behavior. The labels show what developers say they collect, not necessarily what actually happens post - installation. Users should remain vigilant about actual data collection practices once apps are installed and running on their devices.
The systematic evaluation process involves examining each privacy category thoroughly, comparing similar apps’ data practices, and weighing privacy trade - offs against app functionality before making installation decisions.
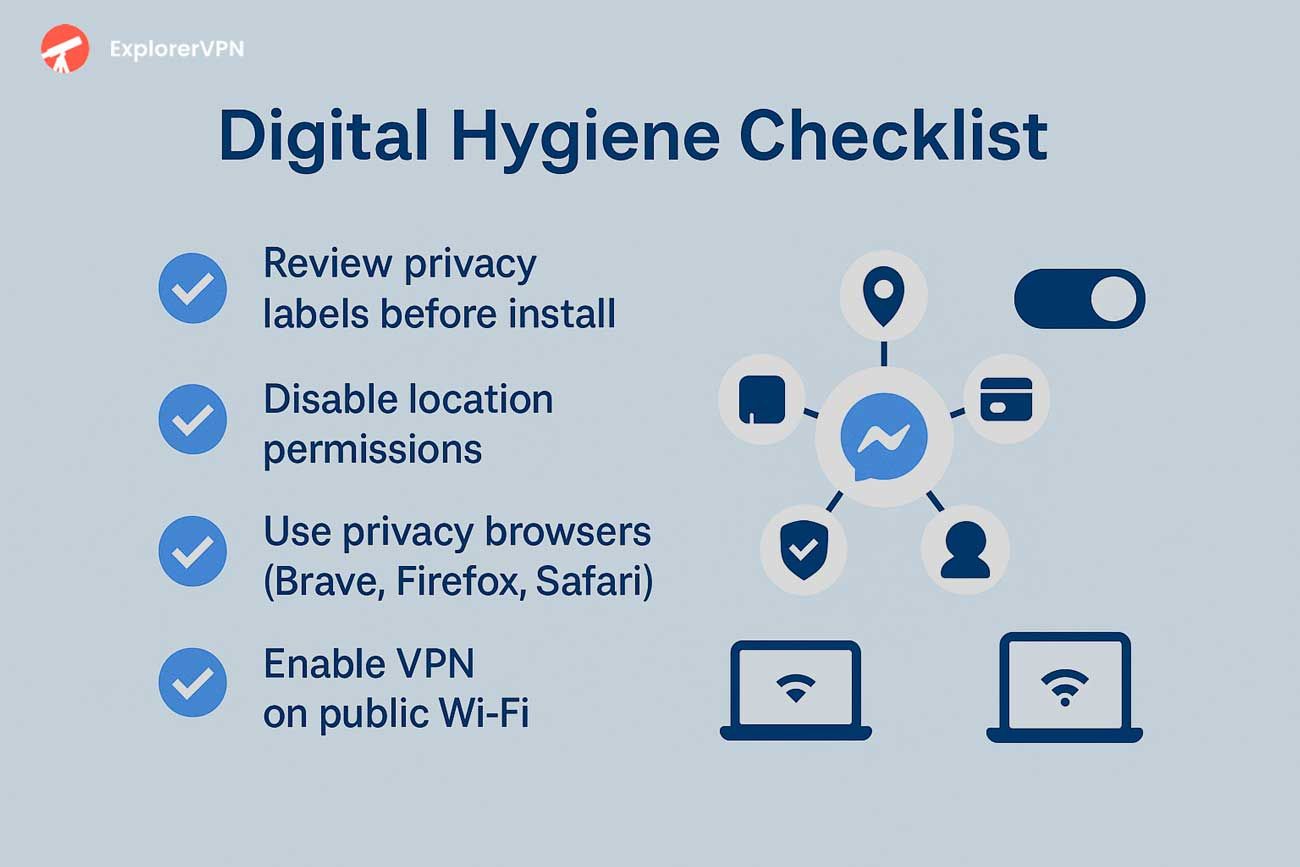
Digital hygiene checklist
Safer Alternatives and Tools (Browser Use, VPNs, Privacy Settings)
Strategic browser choices, VPN services, and enhanced privacy configurations create multiple layers of protection against tracking and surveillance.
Browser privacy performance varies dramatically across platforms. Brave and Firefox achieve 3/3 scores on default privacy features, while Chrome and Edge score 0/3 according to privacy evaluations. Safari delivers optimal performance on Apple devices with integrated tracker blocking capabilities. LibreWolf represents the maximum security option for users prioritizing advanced protection.
VPN selection requires verified no - logging policies and strong encryption protocols from providers. Essential configuration changes include replacing default Google or Bing search engines with privacy - focused alternatives to reduce data exposure. VPNs provide additional security tools such as blocking malicious sites and may include kill switches to prevent IP leaks during connection interruptions. VPNs are essential for students, travelers, and remote workers who frequently connect to public Wi - Fi networks in airports, cafes, and other shared spaces.
PrivacyTests.org provides state partitioning capability evaluations that demonstrate measurable protection against cross - site tracking. Proper browser selection combined with enhanced privacy settings beyond manufacturer defaults creates significant barriers to surveillance and data collection across multiple browsing sessions. VPNs create an encrypted tunnel between your device and a remote server, preventing ISPs and hackers from monitoring your online activities while masking your real IP address.
Worst Apps For Privacy: FAQ's
Can I Permanently Delete My Data From Apps After Uninstalling Them?
No, simply uninstalling apps does not permanently delete all your data from those apps. Complete data removal requires methodical analysis beyond standard app uninstallation procedures. Users must clear app storage and cache before removal and separately contact app servers to request account deletion, as uninstallation alone leaves residual data intact on both your device and the company's servers.
Do Privacy Laws Like GDPR Actually Protect Users From Data Collection?
Yes, privacy laws like GDPR provide partial protection from data collection but do not prevent it entirely. GDPR effectiveness demonstrates measurable protection through €5.88 billion in cumulative fines against major tech companies and mandatory user consent mechanisms that give individuals control over their personal data. However, 30% of European businesses remain non - compliant with GDPR regulations, and data brokers continue operating through legal loopholes, indicating partial rather than thorough data collection prevention across the digital ecosystem.
How Can I Tell if My Data Was Involved in Breaches?
You can tell if your data was involved in breaches by using monitoring services like Have I Been Pwned, which tracks 12 billion compromised accounts across 650+ breaches. Personal data monitoring includes checking security logs, credit reports, and automated alerts to identify if your information has been compromised in data breaches.
Are Paid Versions of Apps Always More Private Than Free Versions?
No, paid versions of apps are not always more private than free versions. Research demonstrates paid vs free app privacy features show minimal differences. Empirical analysis reveals 48% of paid applications retain identical third - party tracking code, while 38% maintain equivalent data collection practices despite consumer payment. Many paid apps continue implementing the same analytics frameworks, advertising SDKs, and user behavior monitoring systems found in their free counterparts, suggesting that payment status does not guarantee enhanced privacy protection or reduced data harvesting activities.
Can Employers Access Personal Data From Work - Installed Apps on My Device?
Yes, employers can access personal data from work - installed apps on your device, but the extent depends on whether you're using a company - owned or personal device. Work - installed applications on company devices have broader access to personal data within their permission scope, including contacts, location, browsing history, and stored files. Personal devices maintain stronger privacy protections, as employers typically cannot access personal data unless you explicitly grant consent through mobile device management (MDM) software or enterprise apps. The specific permissions granted during app installation, device ownership policies, and your employment agreement determine what personal information employers can monitor or collect.